Log Analysis – Log files can be fun!
Haven’t blogged for a while because I’m busy looking at some new technologies and I’m still in beginner mode on most of them.
Today I want to give you an introduction to one of this topics, Log Analysis with the ELK Stack.
But before going into more details in future posts I will just show you some examples of the things you can do with your log file.
1. IBM Domino Console Log:
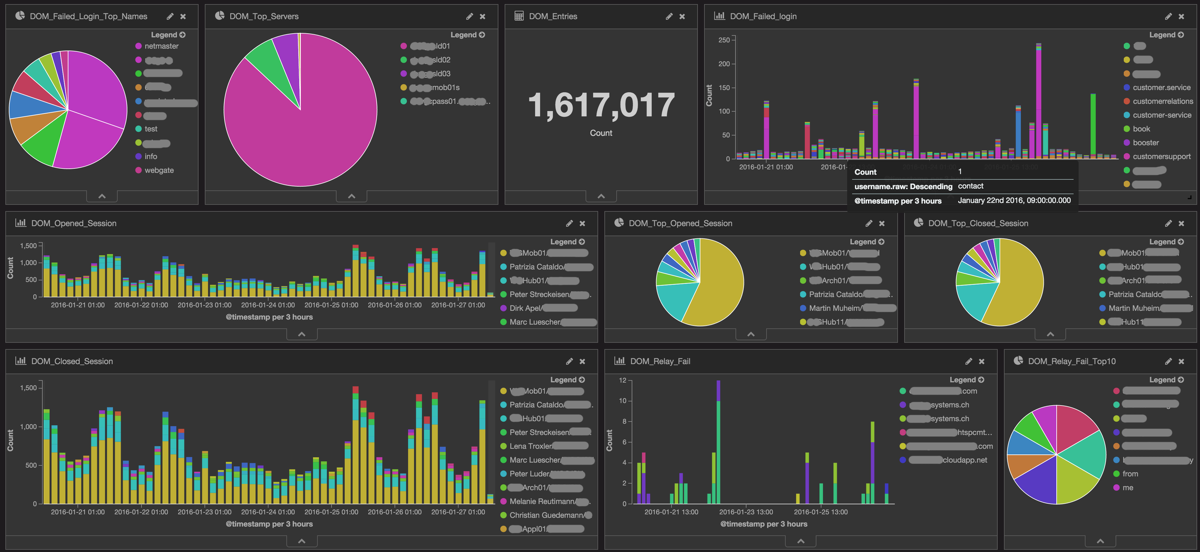
This is what you can create with data inside your IBM Domino console log, you can find visualizations for “Failed Logins – Top Usernames”, “Number of failed Login in a Timeline”, “Opened sessions”, “Closed sessions”, “SMTP Relay fails”…
And all of this is just done with the data which can be found in the log. Of course the graphs and visualizations in this dashboard are clickable and you can drill down to the single log line.
Nice, isn’t it.
2. IBM Connections Logs:
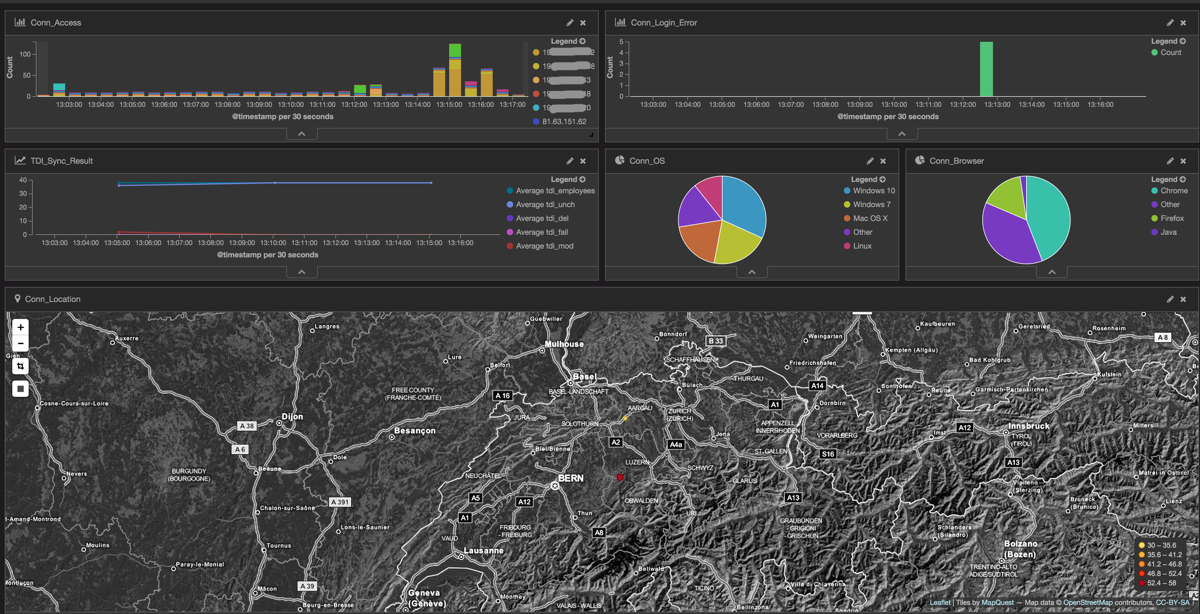
This dashboard uses data from the IHS, WAS and TDI server. You can see how many user session were opened in the last 15min, how many failed logins occurred. You can see the OS, Browsers and Location of the Clients as well. Furthermore I added a visualization of the TDI sync process. I can see how many user were changed, added, modified etc. during the last runs of the sync_all_dns script. This is just a starting, I plan to enhance this dashboard in the future.
3. Firewall Logs:
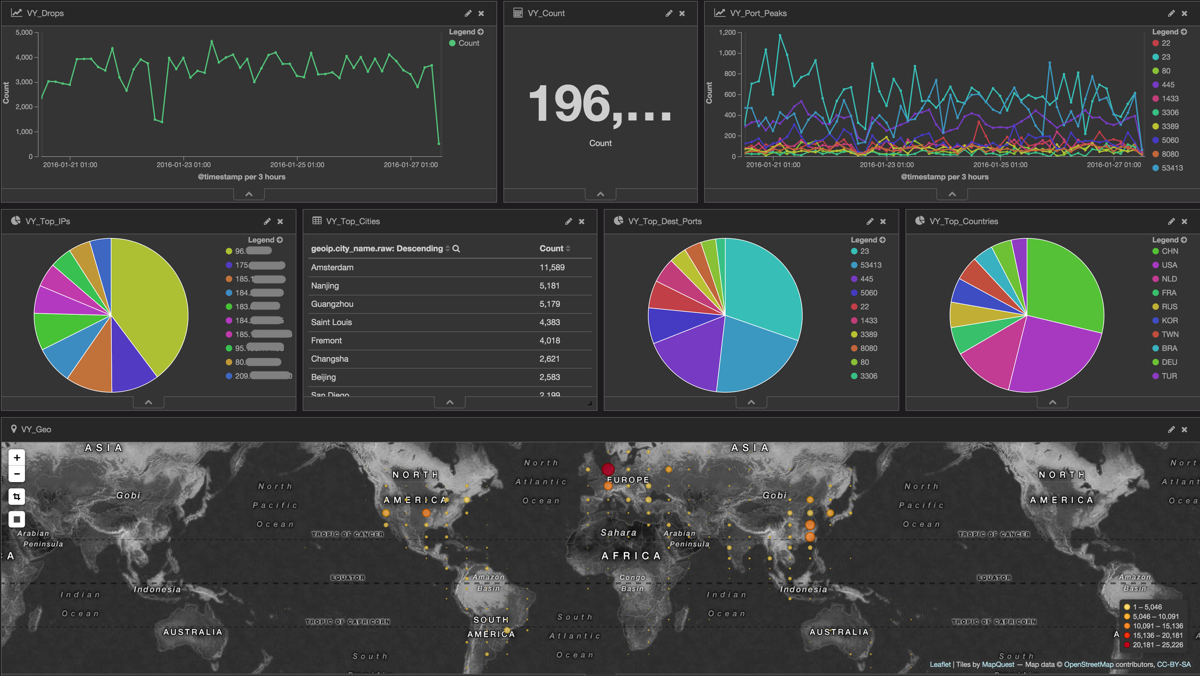
Which ports were tried to access, how many requests were there in the last 7 days, Top 10 Client IPs, Location…
-> I will see all attacks on our network in the future 🙂
4. OS Syslogs:
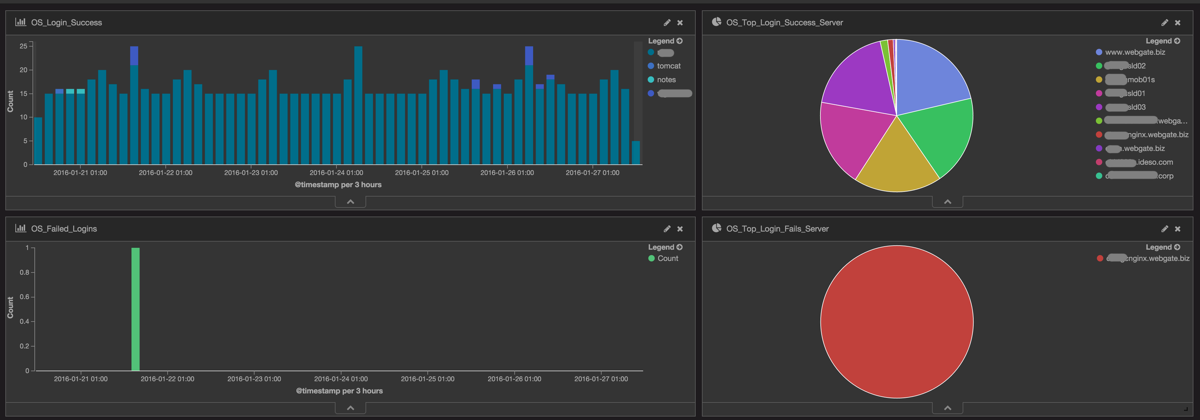
How many logins were on our Linux servers in the last days, which user logged in, on which servers, where there any failed logins and from whom.
As you can see there is a lot of information in your log files, you just have to release it from your logs.
I will be at IBM Connect in Orlando in the next week, if you want to see more of these examples ping me on Twitter.
Together with Victor Toal I plan to show more on this topic at some UG events, hopefully we get our session abstracts approved 😉