Using SSL in Sametime 8.5.x for LDAP connections Part 2
Took me a little bit longer as expected but here is now part 2, how to enable SSL for LDAP connections on the community server.
In part 1 described how you can enable SSL for LDAP connections on the WAS servers.
You can find some information on this topic in the
Sametime Wiki but I found it rather confusing and misleading.
First of all I had to set up iKeyman and the GSKit on the community server to support Cryptographic Message Syntax (CMS) and create the Keystore DBs. We need 3 different Keystore databases:
– CMS Keystore key.kdb -> used by different Sametime server components to connect securely to LDAP server
– Java Keystore stkeys.jks -> used by the userinfo servlet (Business Card) to connect securely to LDAP server
– Keyring File sametime85.kyr -> used by the Domino server (directory assistance) to connect securely to LDAP server
Install GSKit
– Go to the folder where you extracted the Sametime Standard Server Installation files. In there you find a folder “GSKit” – “Win32”. Run gsk8crypt32.exe as Admin
– Use standard values for installation wizard
– Run gsk8ssl32.exe as Admin and use standard values for installation wizard
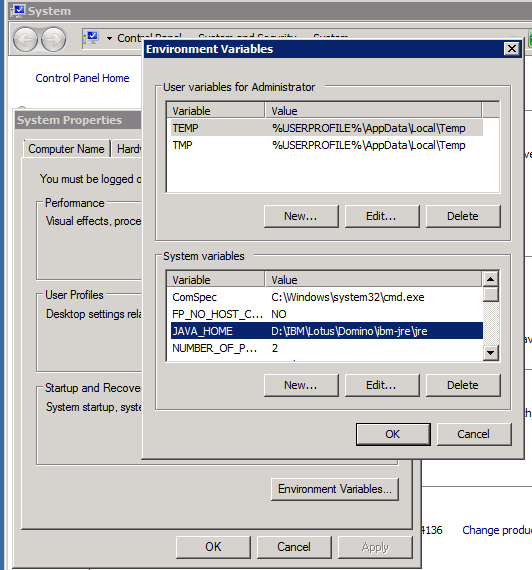
– Add you Domino java folder as JAVA_HOME system variable
Update iKeyman to support CMS
– copy gskikm.jar and ibmcmsprovider.jar from you Sametime System Console (SSC) server to the community server and replace the older ones. You can find these files in the _C:\WAS_INSTALL_DIR\WebSphere\UpdateInstaller\java\jre\lib\ext_ folder. Copy them to _C:\DOMINO_INSTALL_DIR\ibm-jre\jre\lib\ext_ folder.
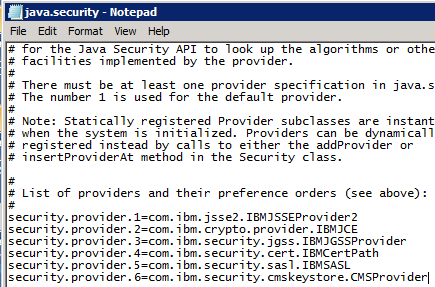
– Edit the file java.security in folder C:\DOMINO_INSTALL_DIR\ibm-jre\jre\lib\security
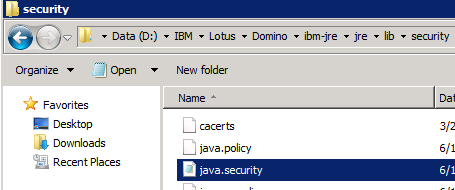
– after _security.provider.5=com.ibm.security.sasl.IBMSASL _add following line:
_security.provider.6=com.ibm.security.cmskeystore.CMSProvider _
Create CMS and Java Keystore files
– Start iKeyman (double click ikeyman.exe) which you can find in C:\DOMINO_INSTALL_DIR\ibm-jre\jre\bin\ folder
– Check the “Help” – “About iKeyman”, you should see
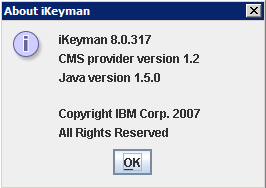
If you see an older Version# check if you copied gskikm.jar and **ibmcmsprovider.jar **from you Sametime System Console (SSC)
– Now create a new CMS database by clicking on “Key Database file” – “New”. Choose CMS as type, name it key.kdb (has to be exactly this name!) and place it in C:\DOMINO_INSTALL_DIR\ (D:\IBM\Lotus\Domino in my example)

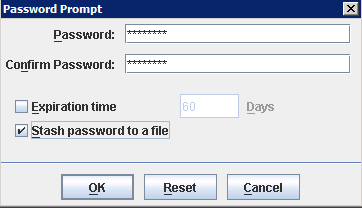
– Define a password and activate “Stash password to a file”
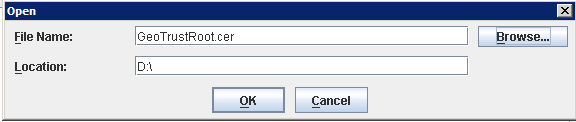
– Go to the “Signer Certificates” and click on “Add”
– Click “Browse” and open the Root.cer file (which you have create before on the SSC Server in Part 1)
– Enter a Label for the Certificate (i.e. GeoTrust Root Certificate)
– Do the same for the Intermediate Certificate
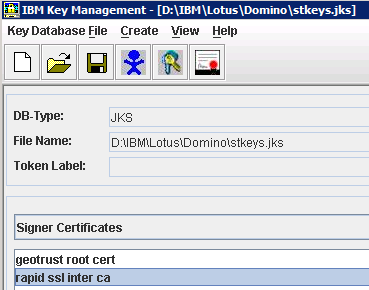
– You should now see 2 Signer Certificates in your keyDB

– Now create a new JKS database by clicking on “Key Database file” – “New”. Choose JKS as type, name it stkeys.jks and place it in C:\DOMINO_INSTALL_DIR\ (D:\IBM\Lotus\Domino in my example)
– Repeat all steps to import the root certificate and the intermediate certificate
Create the Domino Keyring file
– open the Server Certificate Admin DB (certsrv.nsf) on your Community Server with your Notes Client
– click on “1. Create Key Ring” to create a new keyring file
– fill in a name and a password and define your key size

– fill in your server name as Common Name, add your Organization/State/Country and click “Create Key Ring”
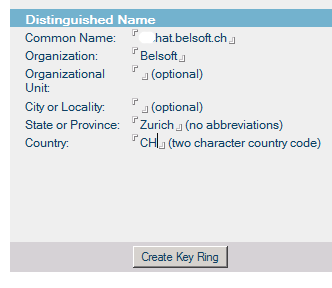
– you will see a confirmation window

– now import your Root Certificate, click on “3. Install Trusted Root Certificate…” and fill in a Label/Source/File Name and choose the appropriate file format
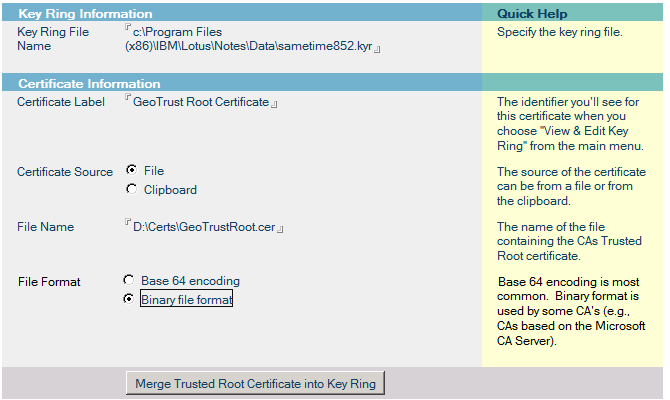
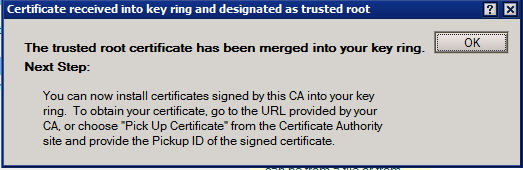
– click on “Merge Trsuted Root Certificate…” and fill in the password for the key ring file
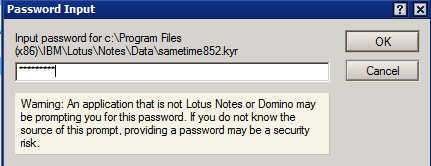
– you will see a success window, click on “OK”
– import your intermediate certificate with same steps
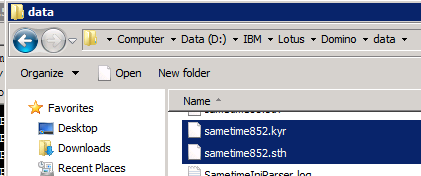
– copy your keyring file and stash file to the data directory of your Community Server
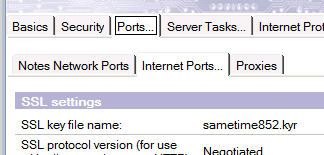
– open the server document of your community server and go to “Ports” – “Internet Ports” and fill in your keyring file name
– save the document and close it
Encrypt the UserInfoServlet
– open UserInfoConfig.xml (in D:\IBM\Lotus\Domino)
– change SslEnabled to true and ensure SslPort is 636
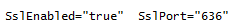
– in the SslProperties tag add the path to your stkeys.jks file and insert your password for the keystore

Configuring Directory Assistance for SSL& Connect Sametime Community Server through SSL
– open the Directory Assistance DB (da.nsf) on your community server with your notes client and change the LDAP settings
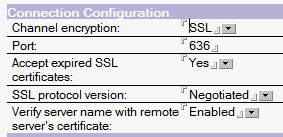
– Click “Save and Close” and close the DB
– Now open the Sametime Community Server webpage and login as Sametime Admin and click on “Administer the Server”
– go to “LDAP Directory” > “Connectivity” and enable the use of SSL for LDAP and ensure that the used SSL port is 636
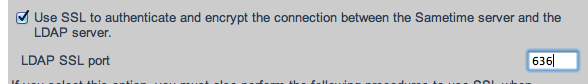
– Click on “Update”
(Optional) If you want to improve performance, you may choose to loosen security and encrypt only user credentials as follows:
– Restart your Community Server
That’s it, now you Security Officer is your friend again!